What is Infrastructure as Code (IAC)?
Stackify in this article introduced IAC like this:
In the past, managing IT infrastructure was a hard job. System administrators had to manually manage and configure all of the hardware and software that was needed for the applications to run.
However, in recent years, things have changed dramatically. Trends like cloud computing revolutionized—and improved—the way organizations design, develop, and maintain their IT infrastructure.
One of the critical components of this trend is called “infrastructure as code”.
Wikipedia defines IaC as follows:
Infrastructure as code is the process of managing and provisioning computer data centers through machine-readable definition files, rather than physical hardware configuration or interactive configuration tools.
In simpler terms,
Infrastructure as code (IaC) means to manage your IT infrastructure using configuration files.
As of today, there are a number of tools that can be used for IAC. Some of which are:
- Terraform
- Ansible
- AWS CloudFormation
- Azure Resource Manager
- Google Cloud Deployment Manager
- Chef
- Puppet
among others.
Objective
In this article, you will understand how Terraform works and how to configure it.
Prerequisites
This article uses the Ubuntu 18.04 Linux distro. That's all the prerequisite you need.
Let's get started.
Terraform
Installation
Add the HashiCorp GPG key
curl -fsSL https://apt.releases.hashicorp.com/gpg | sudo apt-key add -
Add the official HashiCorp Linux repository
sudo apt-add-repository "deb [arch=amd64] https://apt.releases.hashicorp.com $(lsb_release -cs) main"
Update and install
sudo apt-get update && sudo apt-get install terraform
Verify installation by running
terraform -version
If you get this result, then Terraform has been successfully installed.
Terraform v0.14.9
+ provider registry.terraform.io/hashicorp/google v3.60.0
The Terraform version we will be using in this article is v0.14.9 which is the latest version.
Use case
The Terraform use case I'm choosing is the automation of a Virtual Private Cloud using Google Cloud Platform.
Let's get right into it.
Create a directory:
mkdir vpc-with-terraform
Navigate into that directory
cd vpc-with-terraform
Let's start with the main.tf file
nano main.tf
This is a sample of what your main.tf file should look like:
// Configure the Google Cloud Provider
provider "google" {
credentials = file(var.credentials)
project = var.gcp_project
region = var.region
}
// Create VPC
resource "google_compute_network" "vpc" {
name = "${var.name}-vpc"
auto_create_subnetworks = "false"
}
// Create Subnet
resource "google_compute_subnetwork" "subnet" {
name = "${var.name}-subnet"
ip_cidr_range = var.subnet_cidr
network = "${var.name}-vpc"
depends_on = [google_compute_network.vpc]
region = var.region
}
// Firewall Config
resource "google_compute_firewall" "firewall" {
name = "${var.name}-firewall"
network = google_compute_network.vpc.name
allow {
protocol = "icmp"
}
allow {
protocol = "tcp"
ports = ["22"]
}
source_ranges = ["0.0.0.0/0"]
}
We start by configuring the provider which in our case is google.
Next is to provide the credentials. The credentials is fed from a file named credentials.json which we are going to discuss. Next is to provide the project name which will be a variable from an external file. We will also discuss this as we proceed. Same with the region.
As you can see, to use the variables in Terraform 0.14.9, we use the syntax,
var.<variable_name>
When Terraform runs the main.tf file and sees this syntax, it automatically fetches the value from the variables.tf and terraform.tfvars file except otherwise stated (i.e in the case of the credentials where it will fetch the values from credentials.json).
Next, we configure the VPC we want to create.
Here, we specify the resource type and the logical name of the vpc. I'm using "vpc" but you can name it anything. We also specify the actual name of the VPC which is derived from the name variable. Finally, we set auto_create_subnet parameter to false. This is because we want to manually configure the VPC subnets in the regions that we want as opposed to Google automatically configuring the subnets.
Next, we configure the subnets
We specify the resource type, name, IP range, network and region. This is optional but you can add the depends_on parameter that specifies which resource your subnet depends on.
Finally, we configure the firewall rules
Configuring this tells Terraform which protocols your network should be exposed to. Here, I specified icmp and tcp.
Save this file.
Let's create another file. Name it variables.tf
nano variables.tf
This is a typical variables.tf file
variable "region" {}
variable "gcp_project" {}
variable "credentials" {}
variable "name" {}
variable "subnet_cidr" {}
In this file, all the variables used in main.tf are declared. Merely declared. The actual values of these variables are in another file named terraform.tfvars
This is a typical terraform.tfvars file
region = "europe-west2"
gcp_project = "sca-cloud-school"
credentials = "credentials.json"
name = "terraform"
subnet_cidr = "10.10.0.0/24"
Your project name, gcp_project has to be a valid project that exists on your GCP. The other parameters can differ depending on your specification.
Lastly, let's create the credentials.json file.
On GCP, navigate to IAM and Admin. And Service Accounts.
Click the Create Service Account button.
Give it a name and a description (optional).
Add a role (optional)
Create the account.
Open the created account and navigate to the Keys tab.
Click the Add key button. Create New Key. Click JSON.
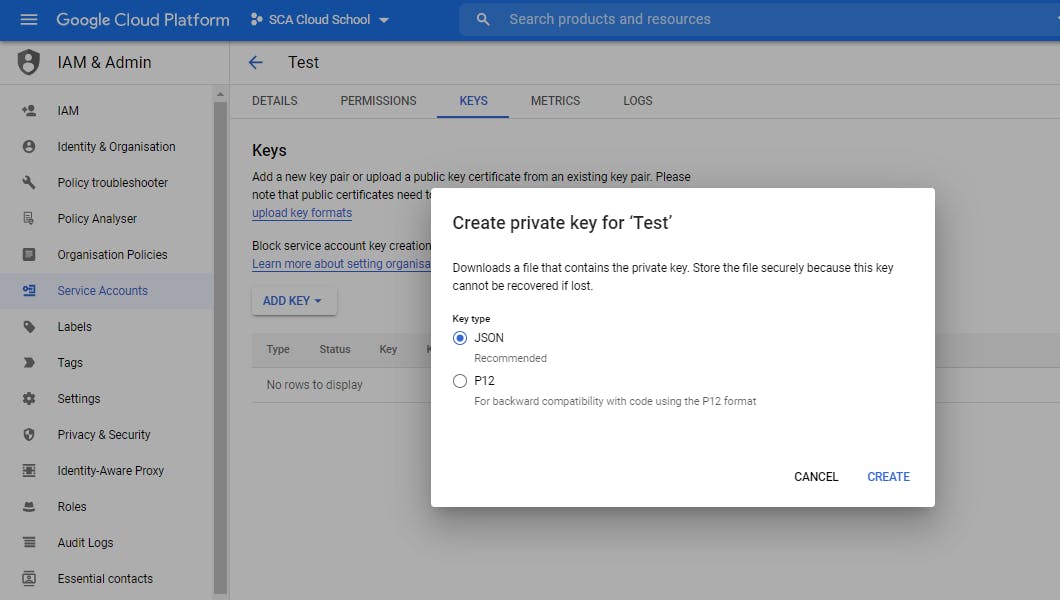
When you click Create, and save the file, copy and paste the entire content of the file to credentials.json
And that's it.
Now we are good to go.
Run
terraform init
to initialize Terraform in your directory
Then run,
terraform plan
This displays all the resources (VPC, subnet and firewall) that will be created at the end of the process.
Finally, run
terraform apply
This creates the VPC, subnet and firewall.
Go to GCP to confirm that the network has been created.
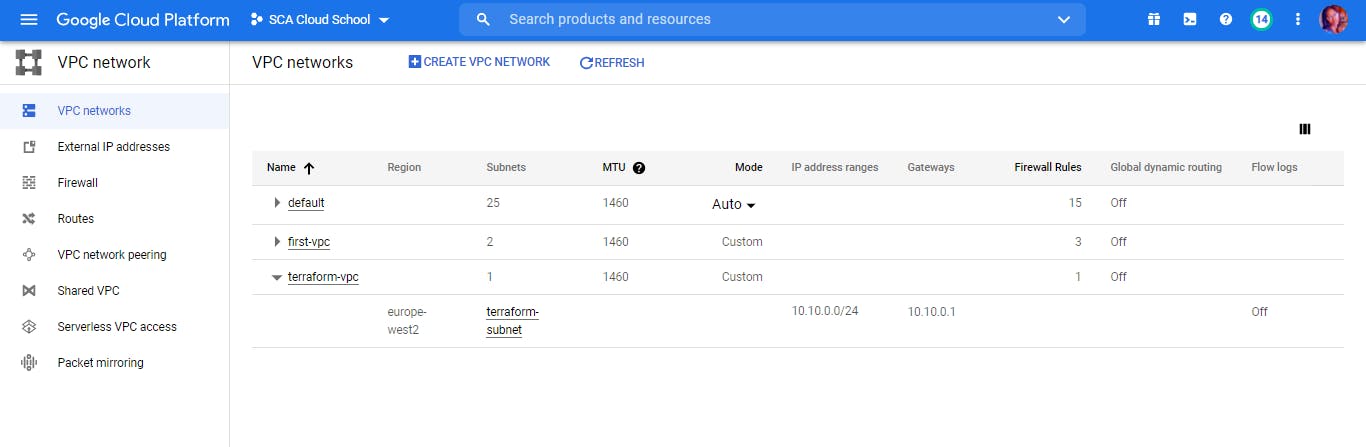
See? terraform-vpc successfully created!
Conclusion
In DevOps, if you need to perform a task more than once, just automate it. And Infrastructure As Code tools are the best use case.
I hope you enjoyed this.
Cheers!
